The best security assessments take an integrated approach, offering organizations and businesses a more comprehensive understanding of the risks they face.

|
January 28, 2025 INSIDE THIS ARTICLE, YOU'LL FIND: |
Organizations large and small are faced with a growing number of unique threats that can evolve and shift as the threat landscape does. For security professionals, the risks that pose the greatest challenge are the ones that slip through the cracks—a physical vulnerability such as a malfunctioning lock on a door, a gap in communication protocols, or a data breach after a software update.
Without a complete understanding of the external threat landscape and of an organization’s vulnerabilities, defenses, and response capabilities, addressing any one threat can become nearly impossible.
A security assessment, also known as a security risk assessment, provides the clarity needed to uncover hidden vulnerabilities and strengthen your defenses. By evaluating areas such as physical infrastructure, digital exposure, and technical systems, a security assessment equips organizations and families with the insights required to protect assets, ensure business continuity, and safeguard their reputations.
What is a Security Assessment?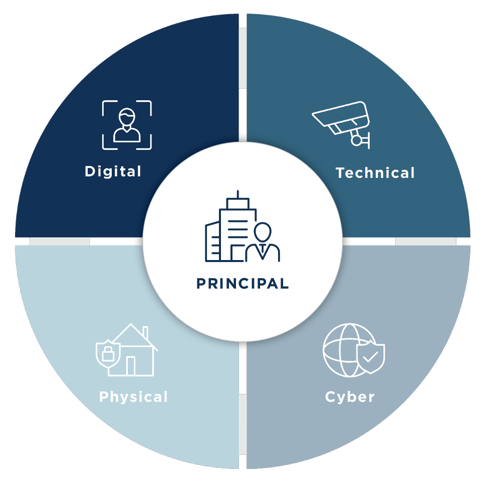
A security assessment is a thorough evaluation of an organization’s overall security posture, aimed at identifying vulnerabilities, mitigating risks, and delivering actionable recommendations.
While a business or organization can conduct any one of these assessments independently to address specific concerns, taking an integrated approach offers a more comprehensive understanding of risk. Threats across physical, digital, and technical domains are often interconnected, and addressing them in isolation can leave gaps in overall security. By evaluating how these domains interact, organizations can create a stronger, more cohesive defense strategy.
This integrated, 360° approach evaluates all aspects of an organization’s security within a unified framework. This methodology identifies vulnerabilities of all types and enables organizations to proactively mitigate risks in today’s increasingly complex threat environment.
Security assessment programs typically involve a multidisciplinary team that may include security professionals, IT experts, facility managers, and leadership stakeholders. The process begins with a detailed consultation to understand the organization’s unique risks and goals. Onsite evaluations, interviews with key personnel, and reviews of current protocols and systems are common components. Depending on scope and complexity, an assessment can take anywhere from a few days to several weeks. The final deliverable is a comprehensive report that outlines vulnerabilities, offers best-practice recommendations, and provides a roadmap for implementation.
Security assessments for individuals and families
It’s important to note that security assessments, while crucial for corporate entities, play an equally vital role in protecting private clients, families, family offices, and their assets. While some high-net-worth families come under the umbrella of corporate protection through C-suite positions, many require standalone security evaluations tailored to their unique circumstances. These private assessments address distinctive challenges like securing multiple residences, managing household staff, protecting family offices, safeguarding children's activities and education, and ensuring privacy during travel or public appearances.
Many families assume they can maintain a low profile through discreet living, but in today's digital age, this perceived anonymity is often illusory. The proliferation of personal identifying information across public records, social media, property databases, and data brokers means that maintaining genuine privacy requires active security measures, not just discretion. Even families who consciously avoid public attention may be surprised by how much of their personal information, asset holdings, and daily patterns are accessible to those who know where to look. In short, there is no "flying under the radar."
Each family's situation demands a customized approach. While corporate and individual assessments may share some common elements, private family assessments require an especially nuanced understanding of personal dynamics, lifestyle considerations, and generational wealth protection.
4 Types of Security Assessments
Each type of security assessment is designed to address specific aspects of an organization’s risk profile, from physical infrastructure to digital exposure. While every assessment serves a distinct purpose, they work together to form a complete picture of an organization’s security posture. Here’s a closer look at the key types of assessments and what they deliver:
Digital vulnerability assessment
A digital vulnerability assessment evaluates an organization’s online footprint to identify privacy risks and exposure across the open, deep, and dark web. This assessment focuses on social media presence, personal information exposure, and potential threats to executives or key personnel. This can help organizations answer crucial questions, such as, “How easy is it to find out where my CEO lives?” and “What personally identifiable information about our c-suite is accessible online?” Almost anyone, no matter how low-profile their lifestyle and activities, has PII exposure that can lead to data breaches, fraud and scams, and more.
Deliverable: A detailed exposure report that highlights digital vulnerabilities and provides clear remediation strategies to mitigate risks, such as privacy setting adjustments, data removal requests, and enhanced monitoring of online activity.
Cybersecurity assessment
Cybersecurity assessments analyze an organization’s digital infrastructure to identify issues that could lead to data breaches, ransomware attacks, or other cyber threats. This involves reviewing network health, endpoint protection, firewall configurations, and the overall security of IT systems. The goal is to pinpoint weaknesses in technology and processes that could compromise sensitive data or disrupt operations. And although many executives enjoy cybersecurity protections in the workplace, their home network is often a key vulnerability that can put corporate IP and important family data at risk.
Deliverable: Actionable insights that detail the current state of cybersecurity, highlight vulnerabilities, and recommend targeted improvements, such as updated firewalls, strengthened endpoint protections, or policy changes to reduce risk.
Technical security assessment
A technical security assessment examines the technical systems that support an organization’s security infrastructure. This includes surveillance systems, alarms, access controls, and monitoring equipment. By assessing the placement, condition, and effectiveness of these systems, this evaluation identifies gaps and opportunities for optimization, ensuring that technical resources are working cohesively to protect the organization.
Deliverable: A comprehensive report with tailored recommendations for upgrading and optimizing technical security systems, including equipment placement strategies, system integrations, and cost analyses for implementation.
Physical security assessment
A physical security assessment focuses on evaluating the safety and security of an organization’s physical premises. This includes analyzing property layouts, access points, emergency response procedures, and the effectiveness of security personnel and protocols. By identifying vulnerabilities in the physical environment, such as inadequate lighting, poorly positioned surveillance equipment, or gaps in access control, this assessment provides the groundwork for creating a safer and more secure facility.
Deliverable: A detailed vulnerability report outlining specific risks and providing best-practice recommendations to enhance physical security. This includes prescriptive remedies, site design enhancements, and strategic improvements to protocols and personnel training.
Want more insights?
Sign up and receive the latest intelligence and information for travelers, businesses, and decision-makers, from Global Guardian's team of experts and leaders.
Why Conduct a Security Assessment?
Conducting a security assessment is more than just a precaution—it’s an investment in an organization’s long-term safety, resilience, and reputation. By identifying vulnerabilities and addressing risks proactively, security assessments provide tangible advantages across multiple areas. From operational efficiency to financial savings and stakeholder trust, the benefits of these evaluations extend far beyond immediate risk mitigation. Below are the key benefits of implementing a comprehensive security assessment:
Operational benefits
A well-executed security assessment enhances an organization's day-to-day operations and overall resilience, providing a clear security road map for executives and security teams to follow for both prevention and crisis response. By streamlining security processes and identifying inefficiencies, organizations can improve emergency response protocols and strengthen business continuity planning. This ensures that teams are better prepared to handle incidents and recover quickly from disruptions, minimizing downtime and operational impact.
Financial impact
Security assessments can have a significant positive impact on an organization's bottom line and shareholder value. By proactively addressing vulnerabilities, organizations reduce the likelihood of costly security breaches, property damage, or data loss, while protecting key executives whose leadership is crucial to shareholder confidence in the organization. Additionally, demonstrating robust security measures can lead to lower insurance premiums, further optimizing security-related expenses and reinforcing the value of preventative action.
Reputational gains
Maintaining a strong security posture signals a commitment to safety and due diligence, which builds confidence among stakeholders, including clients, employees, and business partners. A proactive approach to risk management not only enhances organizational credibility but also safeguards an organization’s reputation in the face of potential incidents. Trust, after all, is an invaluable asset.
What Makes Comprehensive Security Assessments So Valuable
Security threats do not exist in silos—they span physical, digital, operational, and even geopolitical domains. A single assessment can provide valuable insights, but without a comprehensive approach that examines all areas of risk, critical vulnerabilities can be missed.
Regularly conducting comprehensive security assessments ensures that organizations not only address current gaps but also proactively identify and mitigate risks across the full spectrum of their operations. Here’s why this approach is so valuable:
- Uncovering risks across all domains: Threats today are interconnected—what starts as a physical vulnerability can quickly cascade into a data breach, or vice versa. A holistic assessment examines these integration points, from access control systems to IoT devices, uncovering risks that a narrower evaluation might miss.
- Staying ahead of emerging threats: New threats can arise unexpectedly, whether due to advancements in technology, changes in physical environments, or shifts in geopolitical conditions. Consistent security assessments allow organizations to identify these threats early, keeping defenses aligned with the latest risk landscape.
- Adapting to organizational changes: As organizations grow or evolve—adding new locations, implementing new technologies, or expanding their workforce—their security needs change. Regular assessments ensure that security measures keep pace with these developments, preventing gaps that could be exploited by bad actors.
- Reinforcing stakeholder confidence: Frequent assessments demonstrate a commitment to maintaining a robust security posture, which reassures clients, employees, and partners. This proactive approach fosters trust, signaling that security is not just a one-time concern but a continuous priority.
- Strengthening incident response over time: Regular evaluations provide opportunities to test and refine incident response plans. This iterative process ensures that response strategies remain effective, helping organizations recover more quickly and effectively when incidents do occur.
Consistency in security assessments is not just about maintaining the status quo—it’s about building resilience, ensuring preparedness, and creating a culture of proactive risk management. In an environment where the cost of inaction can be high, regular assessments offer the clarity and confidence needed to navigate an ever-changing threat landscape.
Frequently Asked Questions
1. What triggers a security assessment?
A security assessment is needed after significant changes like opening new facilities, adopting new technologies, or responding to emerging threats.
2. Where should an organization start with security assessments?
Start with a comprehensive digital security assessment, which can help identify your most critical vulnerabilities and inform your broader security strategy. The results will reveal your organization's risk level and help prioritize which areas need immediate attention—whether that's system upgrades, additional security protocols, or enhanced protection for key executives and assets.
3. Who benefits most from security assessments?
Organizations of all sizes benefit, but assessments are particularly valuable for businesses looking to prevent costly incidents and maintain stakeholder trust. Smaller organizations in particular gain insights that allow them to allocate resources more effectively.
4. How long does a typical security assessment take?
The timeframe varies but generally ranges from a few days for focused reviews to several weeks for comprehensive, multi-domain evaluations.
5. Can security assessments be customized?
Yes, assessments can be tailored to address specific risks or focus areas, such as physical security, cybersecurity, or digital vulnerabilities. Customization ensures that the assessment aligns with the unique needs and priorities of the organization.
Security assessments are a proactive step toward identifying vulnerabilities, mitigating risks, and safeguarding what matters most. By investing in regular evaluations, organizations can strengthen their defenses, ensure continuity, and build lasting trust with stakeholders.
Standing by to Support
The Global Guardian team is standing by to support your security requirements. To learn more about our Duty of Care membership, as well as business continuity and emergency response planning services, complete the form below or call us at + 1 (703) 566-9463

.png?width=4310&height=881&name=GG-TAssessment-Promo_1-03%20(1).png)


